Overview
This guide walks you through configuring Meter's Network Intrusion Detection System (NIDS) to monitor and protect your network from security threats. You'll learn how to enable detection and prevention, configure which VLANs to monitor, tune severity thresholds, manage categories and signatures, and respond to security events.
Prerequisites
- Meter Firewall (mc06 or mc11) running a NIDS-capable NOS version
- Dashboard access with Partner or Company/Network Admin write permissions
- At least one configured VLAN on your network
- Understanding of your network's security requirements and risk tolerance
Use cases
- Deploy intrusion detection across branch offices to identify compromised devices
- Enable automatic blocking of known malware command-and-control traffic
- Meet compliance requirements for network security monitoring
- Detect and respond to suspicious traffic patterns in real time
- Create custom responses to specific threat signatures
How-to
Enable NIDS
- Log in to Meter Dashboard at https://dashboard.meter.com
- Select the network you want to configure
- Navigate to Firewall > NIDS in the left sidebar
- Click the Config button in the top right
- The NIDS configuration drawer will open
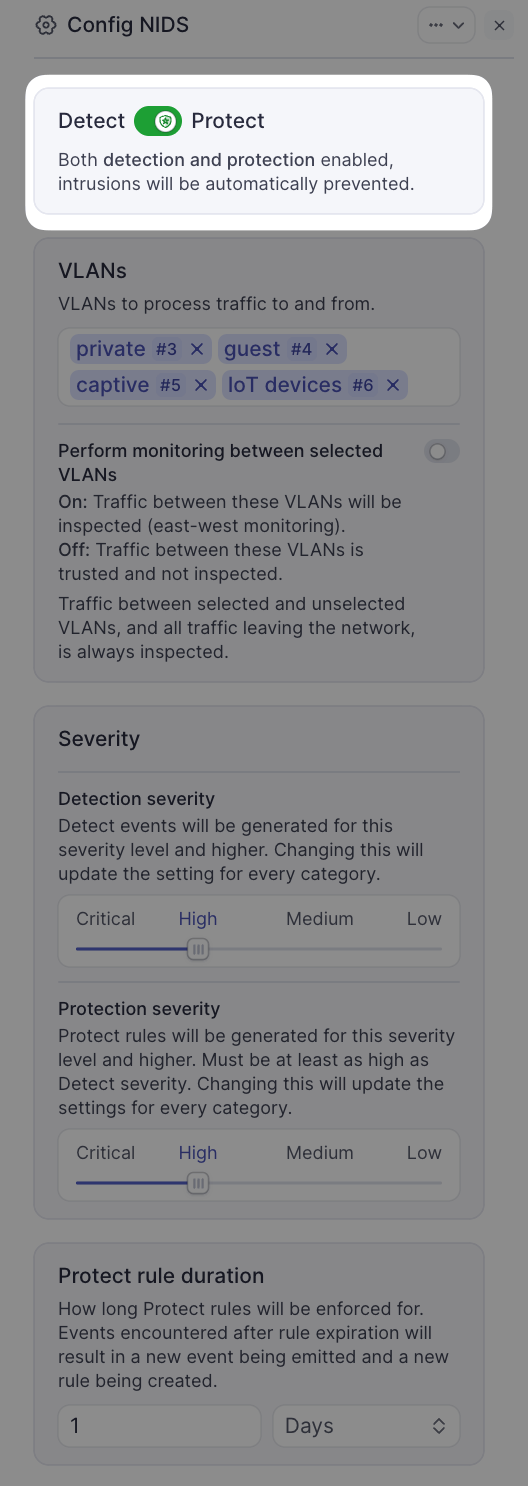
Configure detect settings
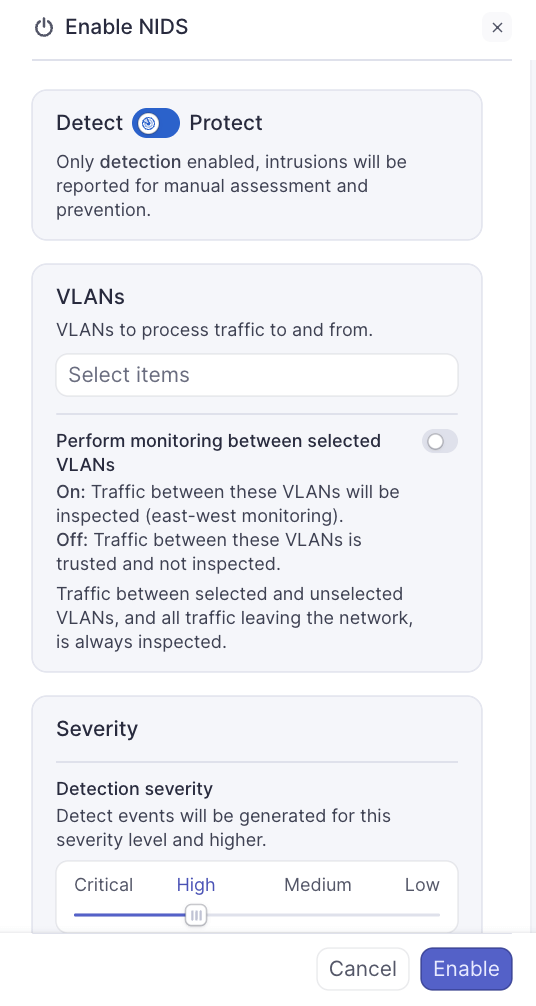
- Mode toggle: Leave the toggle set to Detect for initial configuration
- Detect mode only logs events without blocking traffic
- This allows you to review detection behavior before enabling protection
- Select VLANs to monitor:
- Click the VLANs dropdown
- Select which VLANs should be monitored by NIDS
- Start with business-critical VLANs or those with sensitive data
- You can add more VLANs later
- East-West Detection and Prevention:
- Toggle ON to monitor traffic between your selected VLANs
- Toggle OFF (default) to only monitor traffic entering/leaving the internet
- Enable this if you need to detect lateral movement from compromised devices
- Keep disabled if inter-VLAN traffic is considered trusted
- Detection Severity:
- Use the slider or dropdown to select the minimum severity level to log
- Critical: Only log the most severe threats
- High (recommended): Log significant security concerns and above
- Medium: Include potentially unwanted activity
- Low: Log all events including informational detections
- Selecting "High" means both High and Critical events are logged
- Click Save to enable NIDS in detect mode
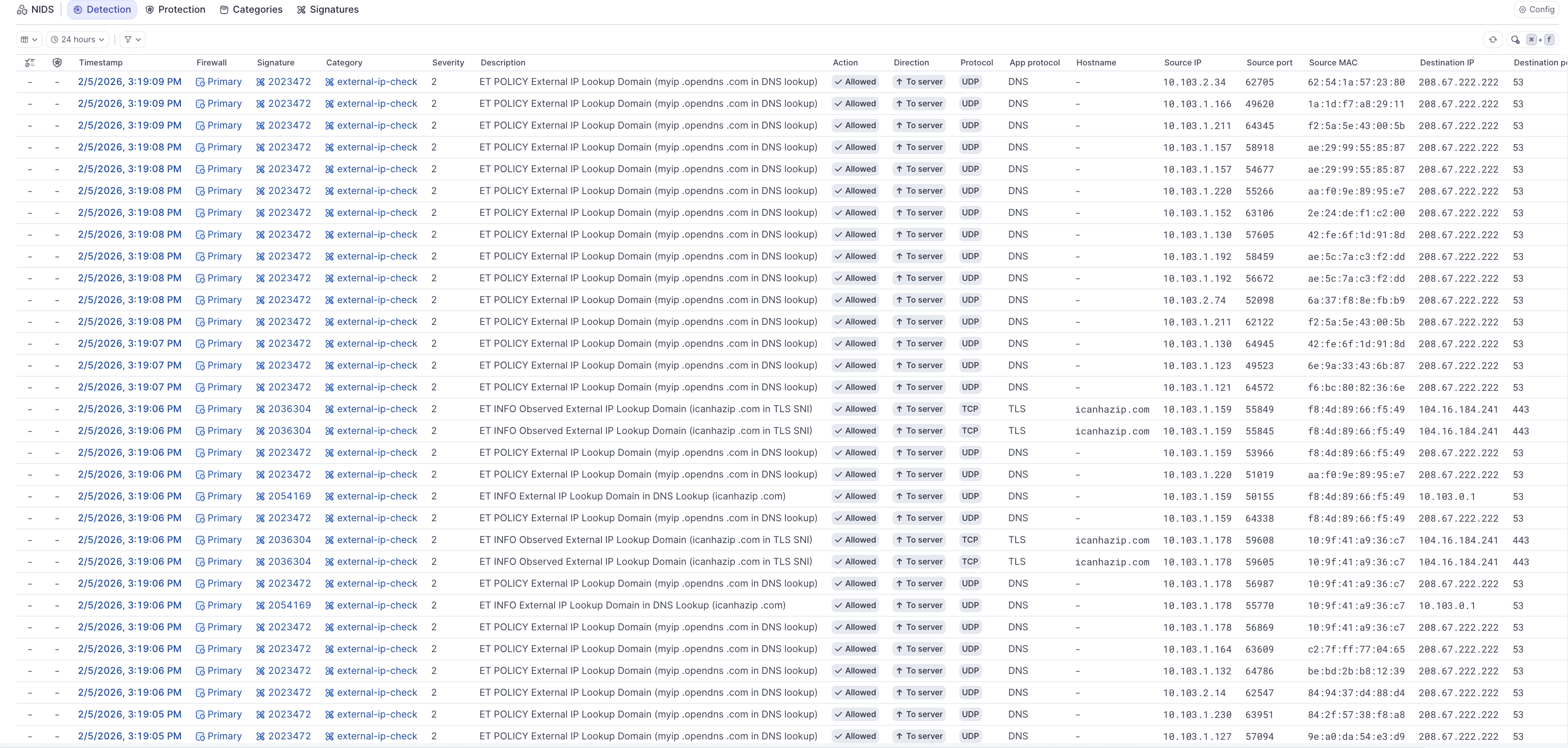
Monitor detection events
- After saving, navigate to the Detection tab
- Wait for network activity to generate events (this may take several minutes to hours depending on traffic)
- Review the events table showing:
- Timestamp of each detection
- Source and destination IP addresses
- Threat category and signature
- Severity level
- Action taken (allowed in detect mode)
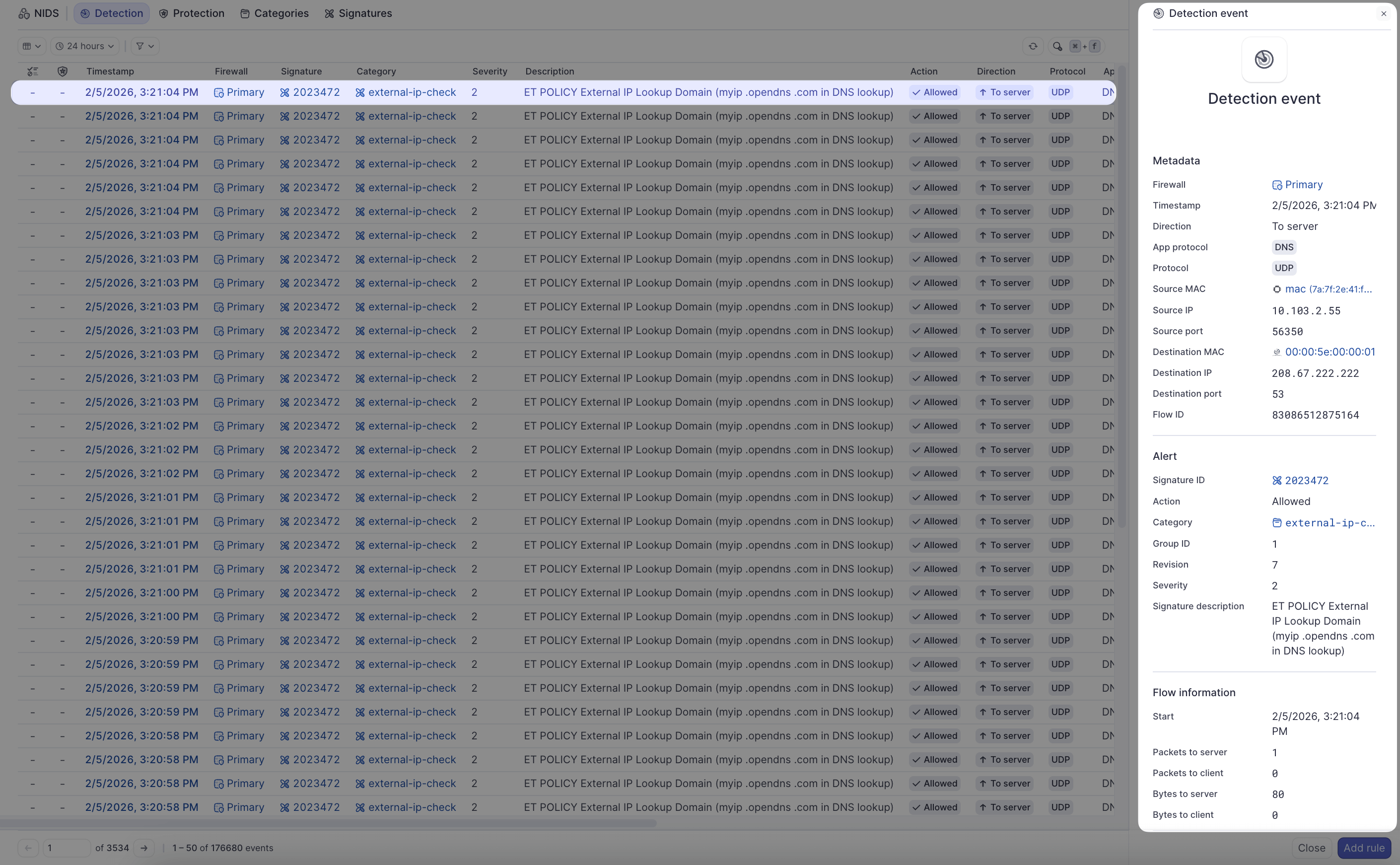
- Click on any event timestamp to view detailed information:
- Full signature description
- Protocol and port numbers
- HTTP metadata (hostname, URL, user agent) if applicable
- Flow statistics (packets, bytes)
- MAC addresses
- Baseline period: Monitor for 1-2 weeks before enabling protect mode
- Identify false positives (legitimate services flagged as threats)
- Review which threat categories are most common
- Verify detection is working correctly
Configure protect settings (IPS)
After monitoring detect mode, enable automatic blocking:
- Navigate to Firewall > NIDS
- Click Config to open the configuration drawer
- Toggle the mode switch from Detect to Protect
- Prevention Severity:
- Set the minimum severity level for automatic blocking
- Critical (recommended): Only block the most severe threats
- High: Block significant security concerns and critical threats
- This operates independently from Detection Severity
- Example: Detect at "High" to log everything, Protect at "Critical" to only auto-block the worst threats
- Protect rule duration:
- Set how long automatically-generated ACL rules remain active
- Default: 24 hours (86400 seconds)
- Range: 1 hour to 30 days
- After expiration, rules are removed automatically
- If the same threat is blocked again, a new rule is created
- Global Protect Suppression:
- Add internal or external IP addresses that should never be blocked
- Enter IPs in CIDR notation (e.g.,
10.103.0.20/32for a single host or10.103.0.0/24for a subnet) - Use this for critical internal services that may trigger false positives
- Detect will still log events from these IPs, but Protect will not block them
- Click Save to enable protect mode
View and manage IPS rules
- Navigate to the Protection tab
- View the table of currently active IPS-generated ACL rules:
- Source and destination IP addresses
- Port numbers and protocols
- When the rule was created
- When it will expire
- Associated threat signature
- To delete an IPS rule before it expires:
- Click the ... (more actions) button for the rule
- Select Delete
- Confirm the deletion
- The traffic will no longer be blocked
Tune categories and signatures
Fine-tune NIDS behavior by adjusting individual categories or signatures:
- Navigate to the Categories tab
- View the list of all threat categories with their current mode:
- Detect: Generate events but don't block
- Protect: Block matching traffic
- Disabled: Ignore traffic matching this category
- Inherited: Use the global detect/protect setting
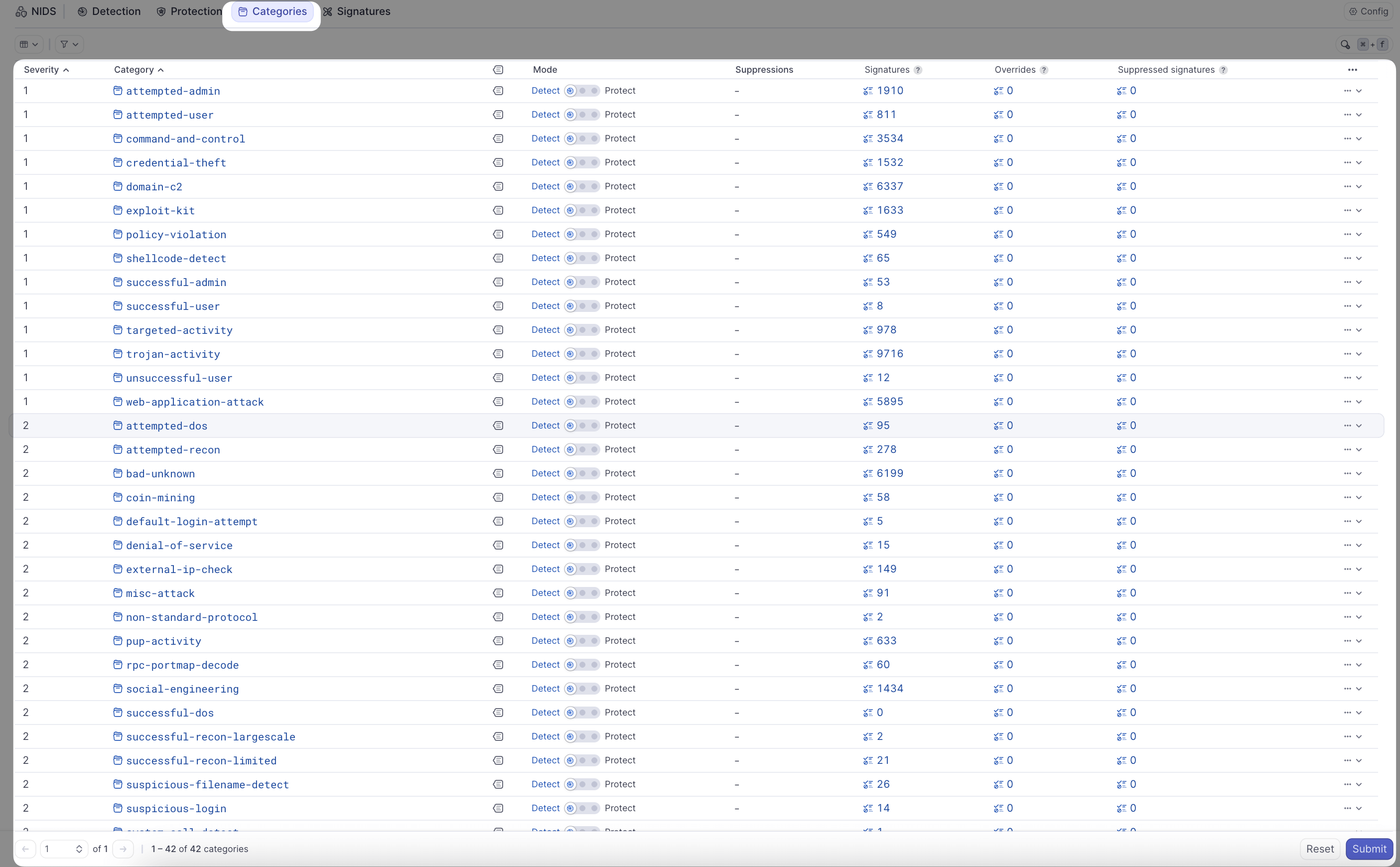
- To change a category's mode:
- Click on the Mode column for the category
- Select the desired mode from the dropdown
- Signature-level settings override category settings
- To configure individual signatures:
- Navigate to the Signatures tab
- Use filters to find specific signatures by ID, name, or category
- Click the Mode column to set behavior for that signature
- Any signature setting overrides its category setting
Create suppressions
Use suppressions to prevent false positives without disabling entire categories:
- Navigate to the Signatures tab
- Find the signature generating false positives
- Click the ... (more actions) button for that signature
- Select Suppressions
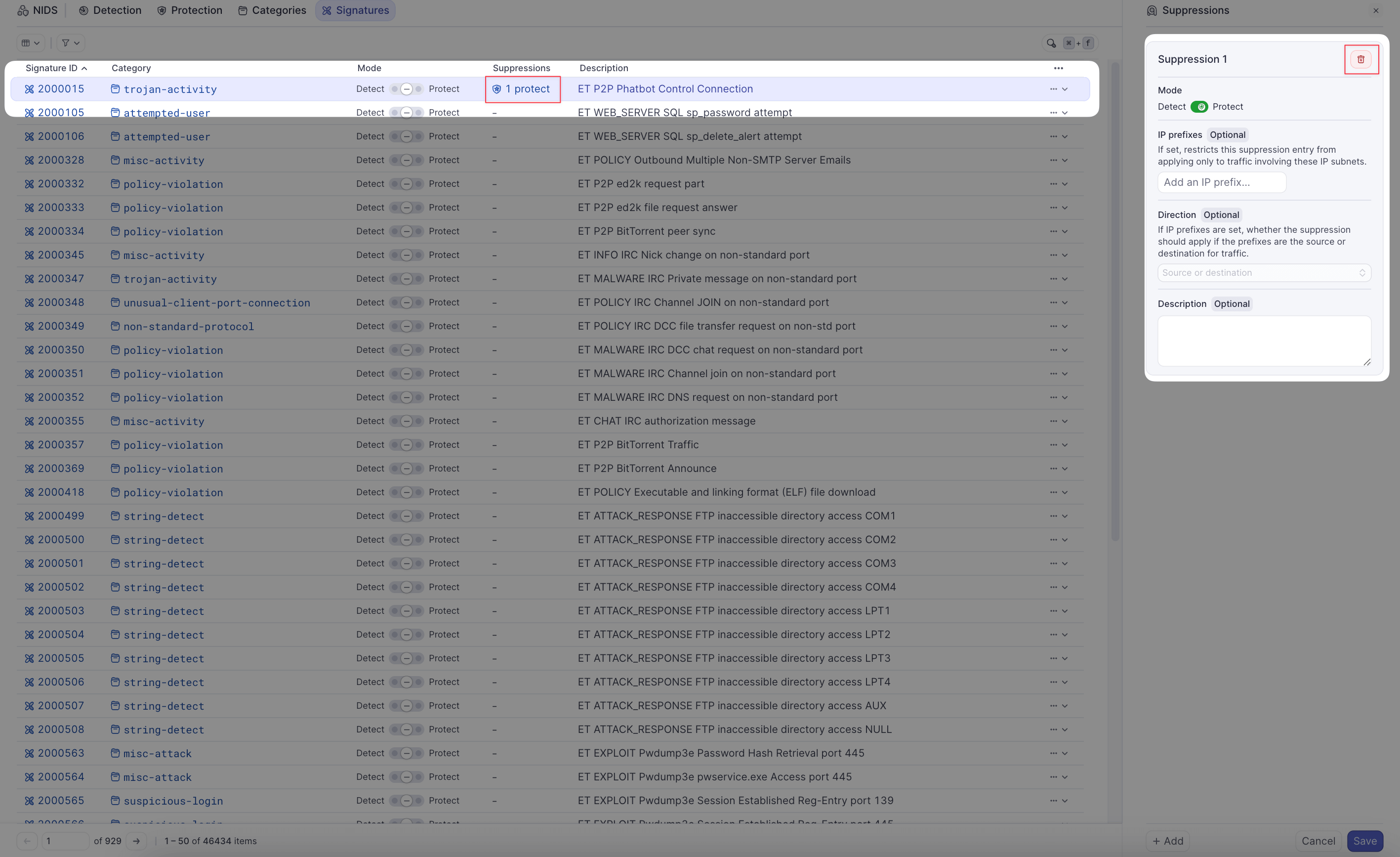
- In the suppression drawer:
- Mode: Choose to suppress Detect, Protect, or both
- IP address: Enter the IP in CIDR notation (e.g.,
10.103.0.20/32) - Direction (optional): Choose if only specific traffic direction should be suppressed
- Both: Suppress regardless of whether the IP is source or destination
- Source: Only suppress when the IP is the source
- Destination: Only suppress when the IP is the destination
- Click Add to create the suppression
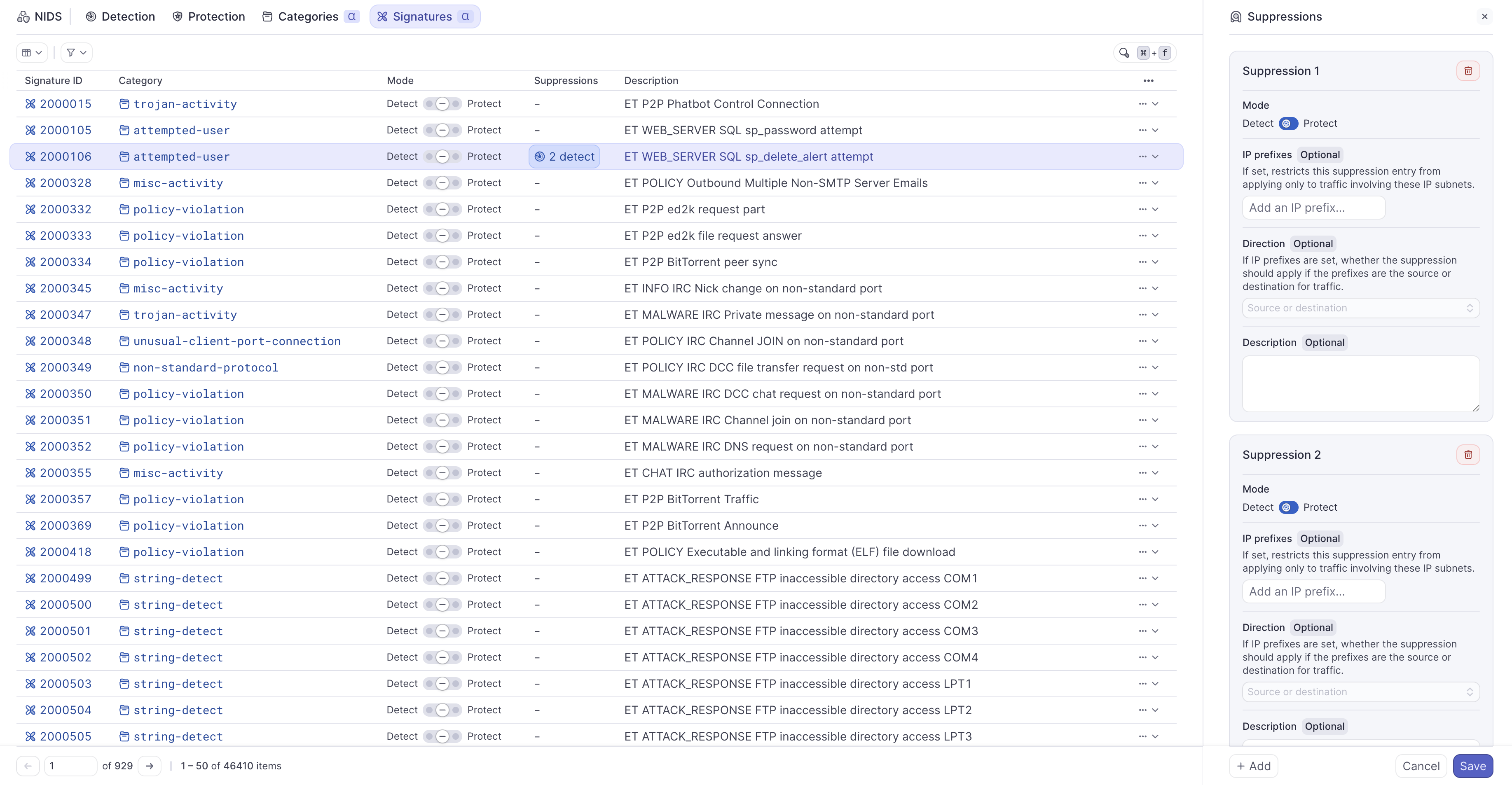
- Review existing suppressions:
- Click on the count in the Suppressions column for any signature
- View all suppressions configured for that signature
- Delete suppressions that are no longer needed
Create permanent ACL rules from events
Convert detection events into permanent firewall rules:
- Navigate to the Detection or Protection tab
- Click on an event timestamp to view details
- At the bottom of the event details, click Create ACL rule
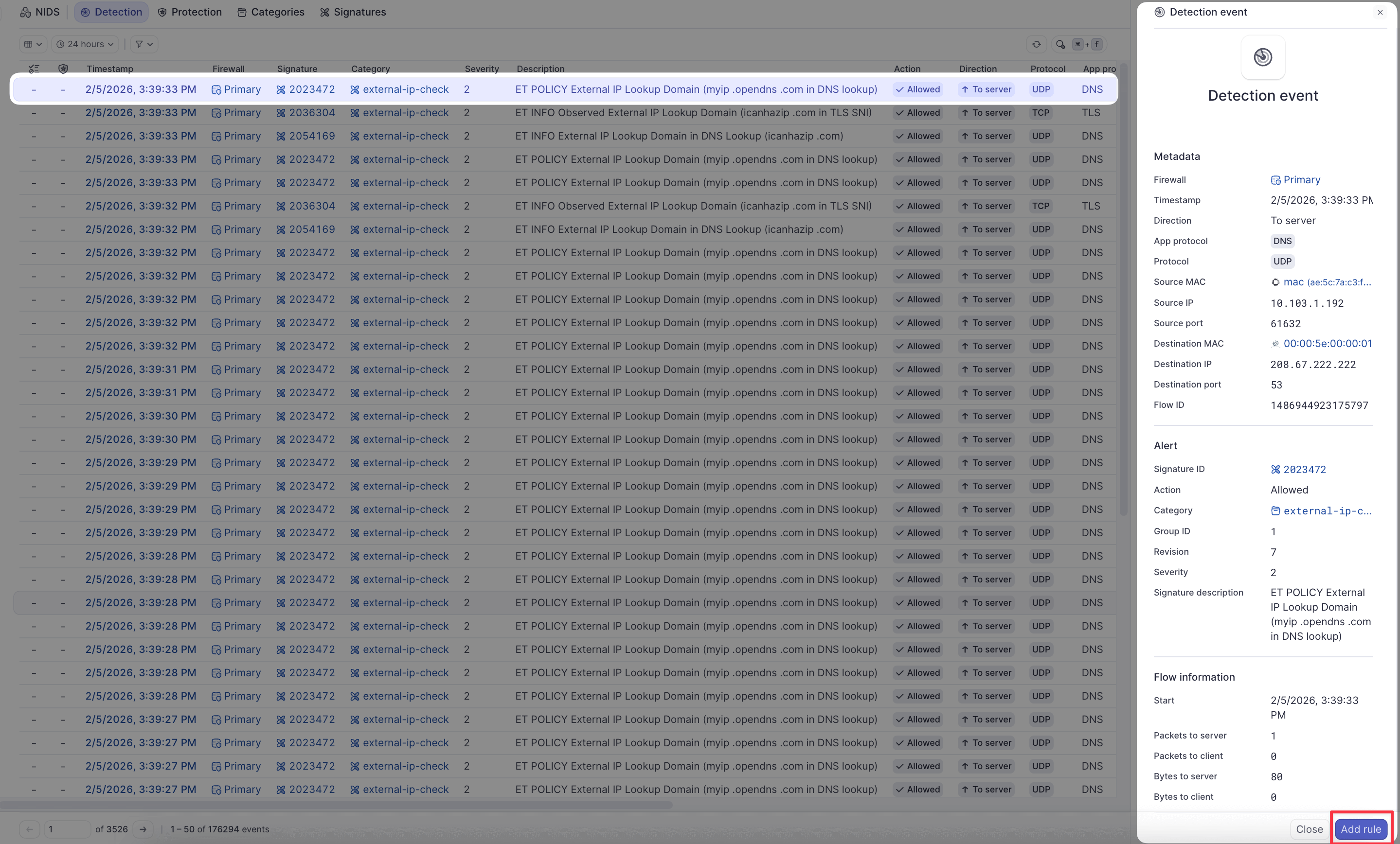
- Edit the ACL rule parameters:
- Adjust source/destination IP ranges
- Modify port numbers
- Add a descriptive name
- Set the rule priority
- Click Save to create the permanent ACL rule
- View NIDS-generated ACL rules:
- Navigate to Firewall > ACLs
- Rules created from NIDS events are marked with a NIDS icon
- Click the icon to view the original detection event
Disable NIDS
If you need to disable NIDS completely:
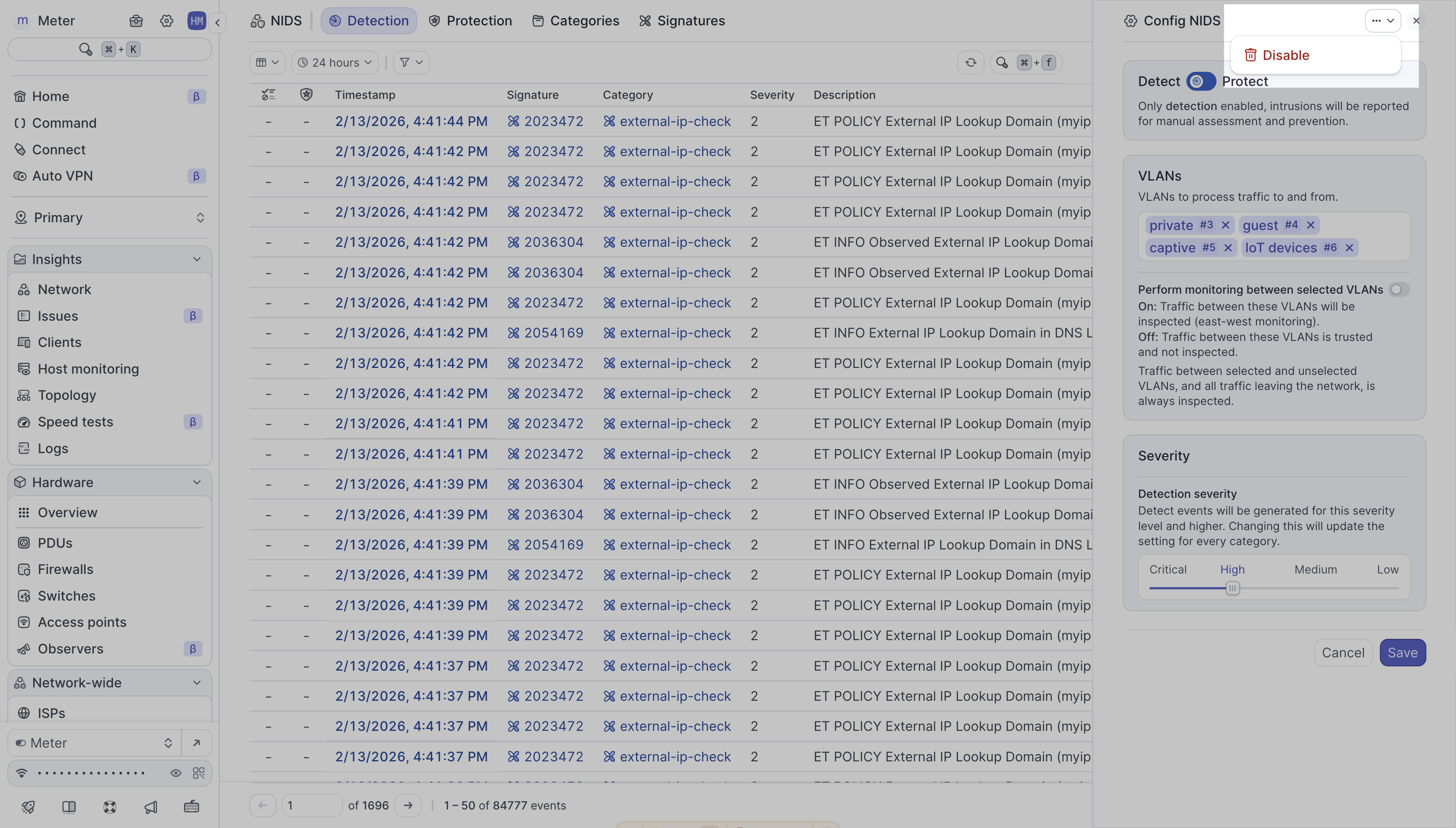
- Navigate to Firewall > NIDS
- Click Config
- Click the ... (more actions) button in the top right of the drawer
- Select Disable
- Confirm the action
- All monitoring and protection will stop immediately
Configuration options
Mode settings
| Setting | Options | Description |
|---|---|---|
| Mode | Detect, Protect | Detect logs events only; Protect logs and blocks threats |
| VLANs | Multiple selection | Select which VLANs to monitor |
| East-West Detection | Toggle | Enable to monitor inter-VLAN traffic |
| Detection Severity | Critical, High, Medium, Low | Minimum severity to generate detection events |
| Prevention Severity | Critical, High, Medium, Low | Minimum severity to automatically block (Protect mode only) |
| Protect rule duration | 3600-2592000 seconds | How long IPS-generated ACL rules remain active |
Category and signature modes
| Mode | Behavior |
|---|---|
| Detect | Generate events, don't block traffic |
| Protect | Generate events and block matching traffic |
| Disabled | Ignore traffic matching this category/signature |
| Inherited | Use the global detect/protect setting (categories only) |
Best practices
Initial deployment:
- Start with Detect mode for 1-2 weeks to establish baseline
- Monitor only 1-2 critical VLANs initially
- Set Detection Severity to "High" to reduce noise
- Review events daily during the baseline period
Tuning for your environment:
- Create suppressions for persistent false positives
- Disable or set to "Detect" for categories that don't apply to your business
- Use category-level controls before adjusting individual signatures
- Document all suppressions and category changes
Enabling Protect mode:
- Set Prevention Severity to "Critical" initially
- Add critical internal services to Global Protect Suppression
- Monitor the Protection tab daily for the first week
- Gradually lower Prevention Severity to "High" after validation
Ongoing maintenance:
- Review detection events weekly for new threat patterns
- Create permanent ACL rules for confirmed persistent threats
- Delete expired IPS rules that are no longer relevant
- Adjust severity thresholds based on event volume and analyst capacity
Troubleshooting
No events appearing in Detection tab
Possible causes:
- NIDS may not yet be fully active (wait 5-10 minutes after enabling)
- Network traffic volume is low
- All traffic is benign and not triggering any signatures
- Selected VLANs have no monitored traffic
Solutions:
- Verify NIDS is enabled in the Config drawer
- Check that VLANs are selected and have active traffic
- Lower Detection Severity to "Low" temporarily to see if any events appear
- Visit a known test site like testmyids.com to trigger a detection
Legitimate service being blocked by Protect mode
Solution:
- Find the signature blocking the service in the Protection tab
- Create a suppression for your internal server's IP address
- Or change that signature's mode from "Protect" to "Detect"
- If the entire category is problematic, adjust the category mode instead
Too many false positive events
Solutions:
- Increase Detection Severity to "High" or "Critical"
- Review the Categories tab and disable categories that don't apply to your environment
- For specific persistent false positives, create suppressions
- Consider whether east-west detection is necessary for your use case
IPS rules persist after expiration
Known issue: IPS rules may still appear in Dashboard UI after reboot, even though they're removed from the Firewall.
Solution:
- Manually delete the rules using the ... (more actions) menu
- The rules are not actually active on the device despite appearing in the UI
Performance degradation on mc11 Firewall
Cause: NIDS limits throughput to under 5 Gbps on 10G Firewalls.
Solutions:
- Disable east-west detection if not required
- Monitor only the most critical VLANs
- Contact Meter support to discuss upgrading hardware if needed
FAQ
Related resources
- NIDS technical overview - Understanding how NIDS works
- Firewall ACLs - Managing permanent firewall rules
- SIEM integration technical overview - Export events to your SIEM
- Configuring SIEM integration - Set up event exports
Need help?
If you run into any issues or have questions, please reach out to our Support Engineering team by opening a ticket via the Dashboard: https://dashboard.meter.com/support
Last updated by Meter Support Engineering on 09/30/2025